Introduction
The Zero Trust Identity and Access Management (IAM) framework is a security architecture that fundamentally changes the way organizations manage access rights. It requires organizations to treat all users, services, and devices as untrusted, regardless of their location or identity. This approach provides organizations with an additional layer of security by verifying the identities of users and devices before granting them access to a system or network.
What is Zero Trust?
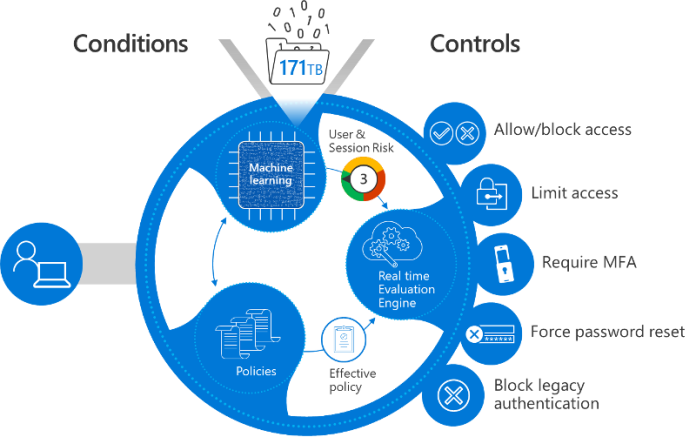
Zero Trust is an approach to security that is based on the idea that no user, service, or device can be trusted by default. All users, services, and devices must be verified before granting them access to the system. The goal of Zero Trust is to reduce the attack surface by eliminating the trust relationship between users, services, and devices.
How Does Zero Trust Work?
The Zero Trust IAM framework works by requiring all users, services, and devices to be authenticated before they can access the system. This authentication process can involve a variety of methods, including multi-factor authentication, biometrics, or other authentication mechanisms. Once the user, service, or device is authenticated, they are granted access to the system.
What Are the Benefits of Zero Trust?
The Zero Trust IAM framework provides organizations with several benefits, including increased security, improved user experience, and reduced cost.
Increased Security: By eliminating the trust relationship between users, services, and devices, organizations can reduce their attack surface. This reduces the risk of malicious actors being able to access the system.
Improved User Experience: By requiring all users, services, and devices to be authenticated, organizations can provide their users with a secure and seamless experience.
Reduced Cost: By eliminating the need for traditional authentication methods, organizations can reduce the cost of managing user access rights.
Conclusion
The Zero Trust IAM framework is an effective way for organizations to reduce their attack surface and increase security. It requires all users, services, and devices to be authenticated before they can access the system, providing organizations with an additional layer of security. Additionally, the Zero Trust IAM framework can reduce the cost of managing user access rights and improve the user experience.