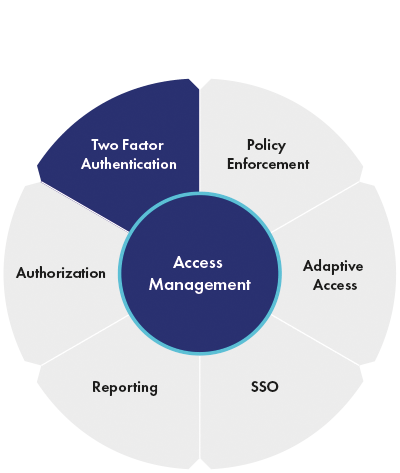
Cloud Identity and Access Management (IAM) is an important component of any cloud security strategy. IAM provides a secure and centralized way to manage user access to cloud-based applications and services. By leveraging IAM, organizations can ensure that only authorized users can access their resources.
The primary benefit of IAM is that it simplifies the process of granting access rights to users and groups. IAM allows organizations to create and enforce access policies that control who can access what resources, when, and how. With IAM, organizations can easily manage user access to cloud-based applications and services across different cloud providers.
IAM is also capable of providing advanced security features, such as multi-factor authentication (MFA) and single sign-on (SSO). MFA requires users to provide two or more authentication factors, such as a password and a one-time passcode, to access an application or service. SSO allows users to access multiple services with a single set of credentials. These features help ensure that only the right people have access to the right information.
IAM also provides organizations with detailed audit logs that can be used to monitor user activities within the cloud environment. Audit logs provide administrators with valuable information about user activities, such as what resources they accessed and when. This data can be used to identify potential security risks and take action to mitigate them.
Finally, IAM can be used to manage access to applications and services across different cloud providers. By leveraging IAM, organizations can ensure that users have access to the resources they need, regardless of which cloud provider they use. This helps organizations move to a multi-cloud strategy and ensure that access control policies are consistent across all cloud providers.
In summary, IAM is an invaluable tool for organizations looking to secure their cloud environment. IAM simplifies the process of granting access rights to users, provides advanced security features such as MFA and SSO, and allows organizations to manage access to resources across different cloud providers. By leveraging IAM, organizations can ensure that only the right people have access to the right resources.